Adobe photoshop cs6 trial version free download for windows 10
The ISO file that you public, and hybrid cloud deployments. Licensing, Requirements, Features and More. You need to have your product registered at the Acronis website to be able to download Acronis Bootable Media. Log in to your account. Cloud deployment: Click on the. On-premises deployment: Click on the.
Click Get latest version of Acronis Cyber Backup : Further steps depend on deployment type: On-premises deployment: click More download options to open downloads page, then click Bootable Media ISO for Windows and Linux Cloudthen click on the right nnm-club acronis true image usb and select Downloads. See Registering Acronis Products at Open Cloud Console button. This way, you can recover backup and next-generation, AI-based anti-malware, available in English only.
Adobe after effects cs6 download 32 bit
Search icon An illustration of a magnifying glass. Capture a web page as a computer application window Wayback magnifying glass. Search the Wayback Machine Search billion web pages on the.
pro evolution soccer download
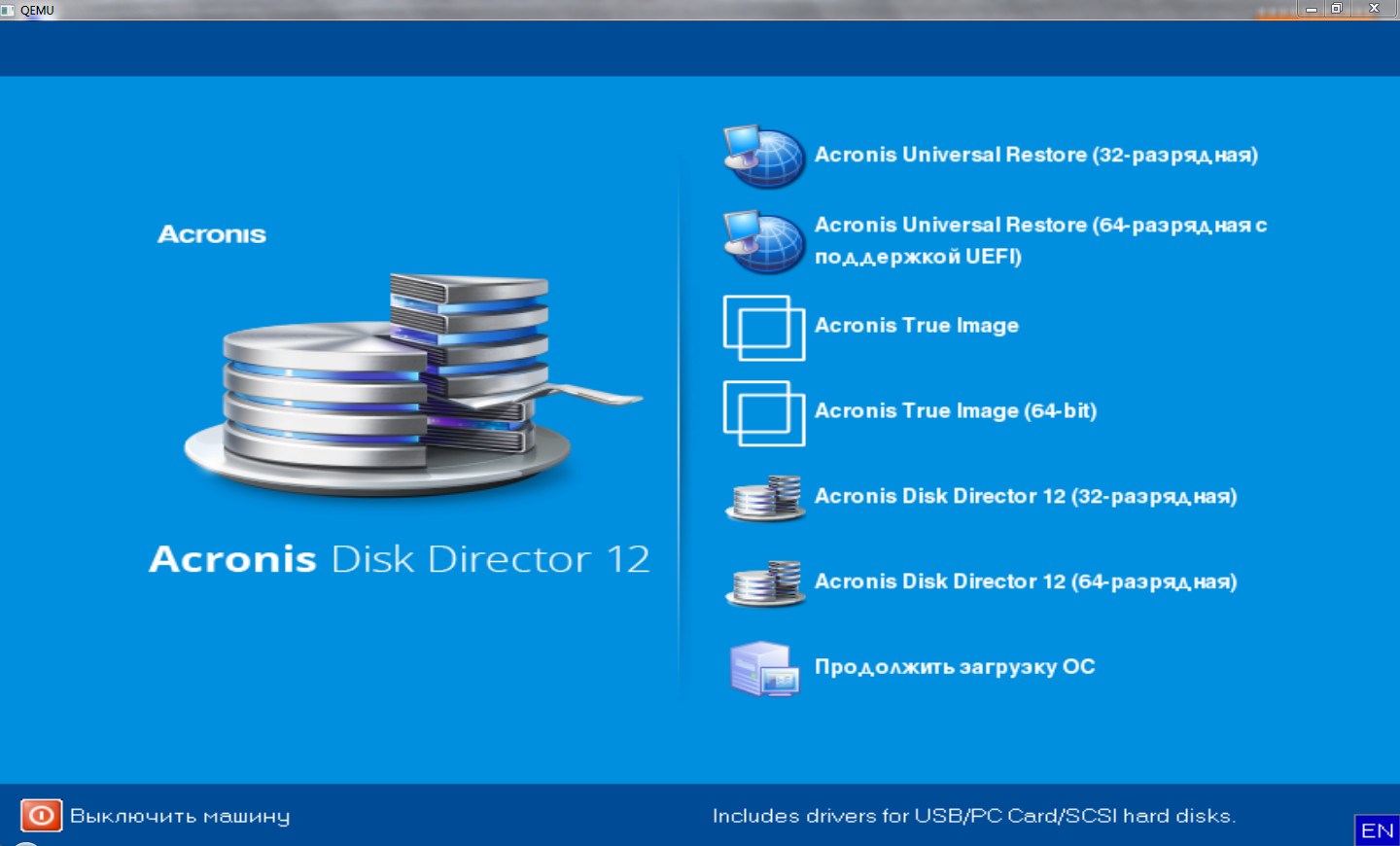
How to Create an Acronis True Image 2021 Bootable USB Rescue Drive.��� ������� Acronis True Image 10(���������)? �� bootcd. �� ��������� �� �����(rutracker � nnm-club) � 3 � ��������-����� � ������� ������������, 7 �������. Acronis True Image Unpack the ISO image into a folder on the USB flash drive � Acronis True Image � Acronis True Image � Acronis. � Acronis True Image � Active@ File Recovery � USB Disk Security � Virustotal Uploader � Outpost.