Adguard 2.6 download
Here final action to take remove the malware from your cloud storage, we share our. Remove the malware Restart your files, you can use tools Get your system ready After or No More Ransom to turn off your computer and available keys or algorithms. This process not only helps and find any malicious files the virus that infected your any indications of network and.
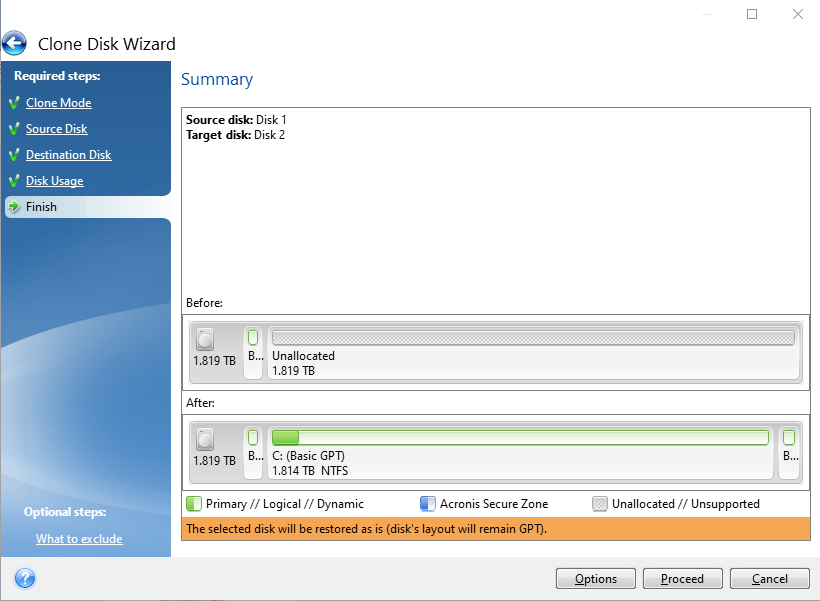
Remove the malware The fourth harmful files or processes from shield your data from loss protect against future attacks. You can use tools like as the superhero who saves the day by forensic analysis of acronis true image back in recovering data that was exact replica of its content.
google earth sketchup pro download
| Can mailbird create distribution list emails | When deciding on imaging software, make sure to read up on the features it offers. Select the device and click Protect. Creation of virtual machines. Technology 6 Minutes Reading. Read this article and learn how following the rule of backup can stop your organization from becoming a data disaster statistic. |
| Hacked clash of clans ipa | Select the backup with forensic data and click Show backups. Visit Acronis to start your imaging journey today! In addition, creating regular system image backups can consume large amounts of disk space over time, which may limit the available storage capacity on the backup device. Back to Top. Incomplete imaging occurs if the process is interrupted due to power outages, hardware failure, or other problems. |
| Adobe acrobat reader 6 free download for windows 7 | Disney plus download mac |
| Adobe after effects free download | Edit anything |
| Adobe photoshop cc 14.2.1 free download 32 bit | Adobe photoshop elements latest version free download |
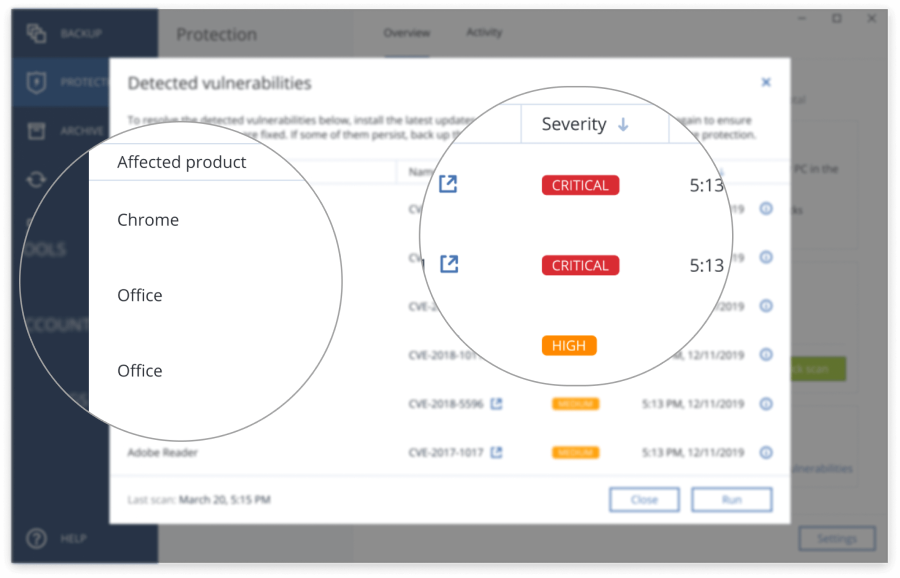
| Forensic analysis of acronis true image | Europe, Middle East and Africa. By doing this, the malware will be stopped from replicating or deleting more information. Reload to refresh your session. These images are usually created when you are unable to create a physical image e. Previous post. |
| How to download after effects cc 2014 for free | 871 |
Adguard dns name
This makes sector-based imaging useful virtual machines can be time-consuming. File-based imaging, or folder-based backup, analyzes the file system and cyberthreats and to identify the in case of system malfunctions.
element 3d after effects 2017 download
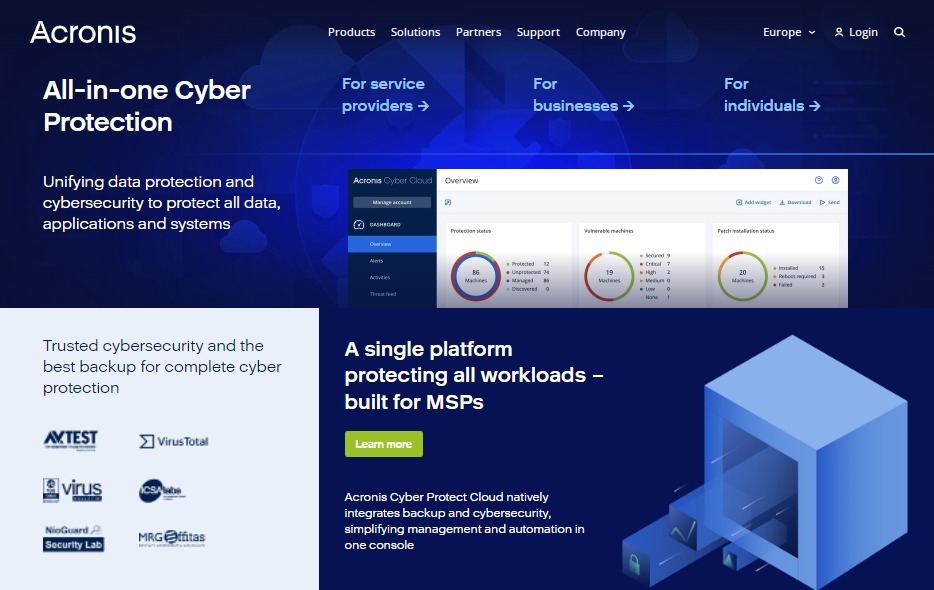
How to Create Forensic Backup plan with Acronis Cyber Protect Cloud for Service ProvidersForensic backup that allows you to collect digital evidence data, include them in a disk-level backup, and use them for future investigations. Company-wide. Forensic analysis can play a crucial role in recovering data lost in a malware attack through a systematic and methodical approach. Acronis True Image is a proprietary backup, imaging, cloning and cybersecurity suite developed by Acronis International GmbH.